Robert N. M. Watson
|
University of Cambridge William Gates Building 15 JJ Thomson Avenue Cambridge CB3 0FD United Kingdom |
Office: GE-13, William Gates Building Voice: +44 (0)1223 763 569 Fax: +44 (0)1223 334 678 E-mail: robert.watson AT cl.cam.ac.uk |
I am Professor in Systems, Security, and Architecture at the University of Cambridge Computer Laboratory. I am involved in several research groups at the lab, including Security, Networks and Operating Systems, and Computer Architecture. I lead a number of cross-layer research projects spanning computer architecture, compilers, program analysis, program transformation, operating systems, networking, and security.
I have strong interests in open-source software, am on the board of directors of the FreeBSD Foundation, and have contributed extensively to the FreeBSD Project. I am a coauthor on the Design and Implementation of the FreeBSD Operating System (second edition) published by Pearson.
I completed two and a half years of post-doctoral research at the Computer Laboratory, and a Research Fellowship at St John's College, Cambridge, in May, 2013 to take up a lectureship in the department. I finished my PhD in Computer Science at the Computer Laboratory in 2010 (awarded in 2011), supervised by Professor Ross Anderson. Prior to that, I worked for six years in a series of industry research labs (SPARTA ISSO, McAfee Research, NAI Labs, and Trusted Information Systems) investigating operating systems, networking, and security; my contributions included widely used work in operating-system security extensibility, the topic of my later PhD dissertation.
My undergraduate degree is in Logic and Computation, with a double major in Computer Science at Carnegie Mellon University. While at CMU, I worked on research projects with Professor M. Satyanarayanan and Professor Jeremy Avigad.
If you are interested in joining my team to work on an MPhil or PhD research project, do see below.
Recent news
- April 2021
I'm very pleased to have received the EuroSys Jochen Liedtke Young Researcher Award at EuroSys 2021 for my work in systems research.
- May 2020
Our paper, Cornucopia: Temporal Safety for CHERI Heaps. appeared at the IEEE Symposium on Security and Privacy in May 2020. This paper describes a GC-like sweeping revocation algorithm, with hardware acceleration, for use with the CHERI architecture. Its hardware dependencies appear in Arm's Morello processor, shipping in 2022.
- February 2020
Our paper, Rigorous engineering for hardware security: Formal modelling and proof in the CHERI design and implementation process, will appear in the IEEE Symposium on Security and Privacy in May 2020. This paper describes our formal modeling and proof work around the CHERI-MIPS architecture, which is one of the foundations for our formal work around Arm's Morello board.
- September 2019
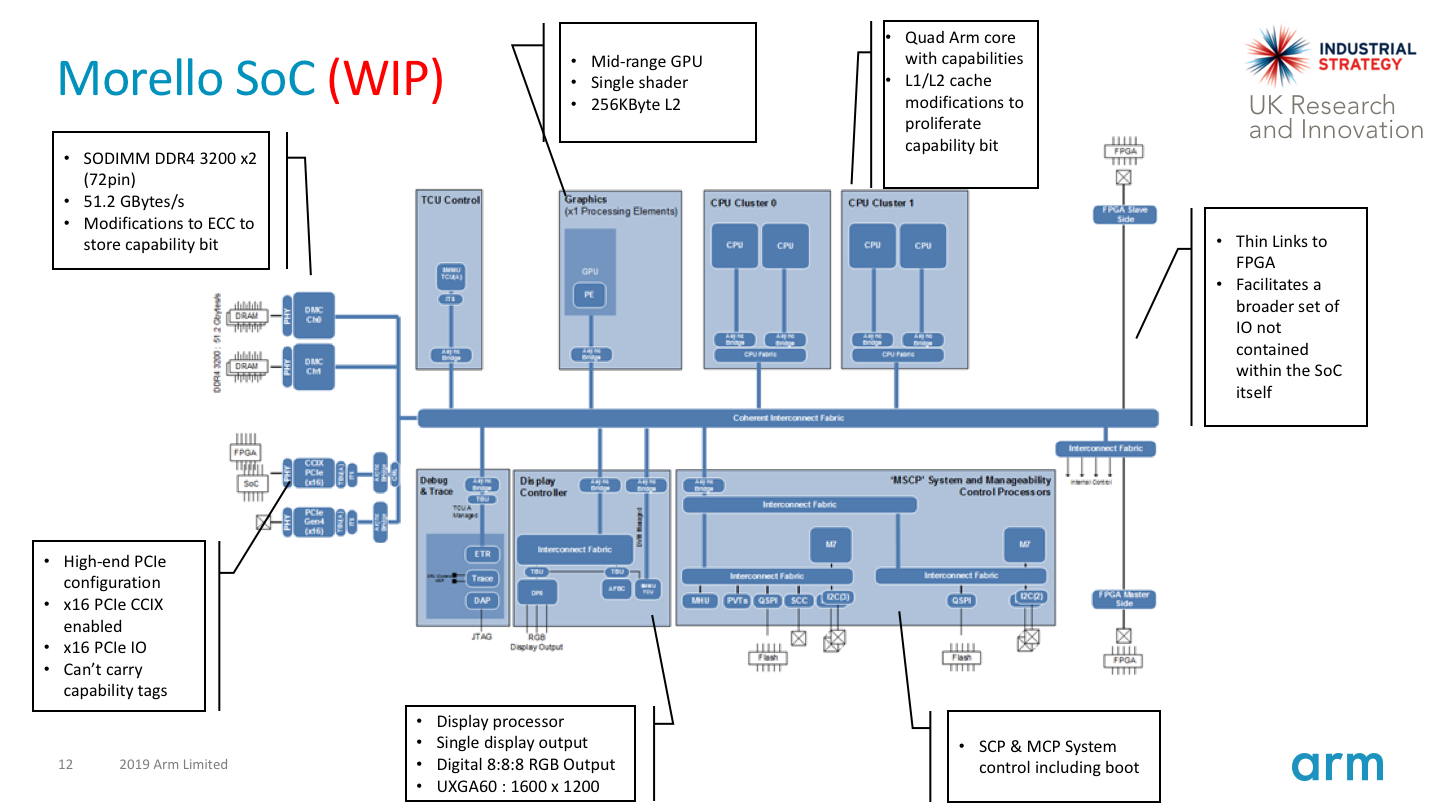
Arm has announced Morello, a CHERI-extended A76-derived processor, System-on-Chip, and development board. Morello will be an industrial scale demonstrator of a capability architecture, fabricated using a 7nm process, providing a quad-core, 2GHz processor based on the A76, suitable to perform CHERI-related research and prototyping in academia and industry. This £187M (~$225M) research programme is supported in part through £70M in grants from the UK Industrial Strategy Challenge Fund, and support from industrial sponsors including Arm, Google, Microsoft, and Amazon.
Applying to our masters or PhD research degrees
If you are applying to our PhD in Computer Science, please review the PhD application information. Once you have reviewed this, if you believe that I would make an appropriate supervisor for your proposed research, please contact me directly well in advance of our annual early December deadline. Please include a recent CV and initial research proposal (contents described on the application PhD web page).
It is a particularly exciting time to work with us on CHERI, with Arm's CHERI-extended Morello board due in early 2022. Areas in which I am particularly soliciting potential research students include:
- Designing, prototyping, and evaluating new software models for memory safety and softawer compartmentalization based on CHERI and Morello.
- Theoretical and practical work exploring the security properties of the CHERI architecture and its software stack.
- The application of CHERI C/C++ memory safety at a larger scale, and to complex software stacks such as language runtimes.
- Performance analysis and optimization techniques for CHERI C/C++-enabled operating systems and applications.
- Software compartmentalization using CHERI, including motivations, techniques, and evalaution, with a particular concern with how and why we compartmentalize software, and benefits/costs in terms of performance, program complexity, security, and maintainability.
- New techniques and approaches to software debugging and tracing in CHERI-based software environments.
- CHERI's interactions with hardware accelerators including GPUs and machine learning, both respect to hardware and software.
Projects and research
Current and recent projects include:
CHERI, a DARPA-funded project in collaboration with SRI International revisiting the hardware-software interface to improve security.
We have designed a new architectural protection model, CHERI, that extends commodity RISC instruction sets with support for fine-grained, compiler-directed memory protection, and scalability, fine-grained software compartmentalisation.
Arm has announced Morello, a multicore superscale CHERI-extended processor, SoC, and development board shipping in 2021.
Read about CHERI in our Introduction to CHERI or CHERI Instruction-Set Architecture (version 7 technical reports.
As part of this work we also developed SOAAP, a set of static analysis techniques to assist programmers in developing compartmentalised software design, implementation, and maintenance.
CADETS, a DARPA-funded project in collaboration with BAE Systems and Memorial University Newfoundland, to improve support for local and distributed tracing via software instrumentation. We are developing a distributed version of DTrace, new LLVM-based program instrumentation techniques, and using architectural simulation tools such as Gem5 to explore optimising the performance of software instrumentation.
This project builds on our prior work on TESLA, a temporaral assertion system allowing us to validate complex safety properties of C-language software, published at EuroSys 2014.
A variety of work in network-stack performance and optimisation, including work on the Sandstorm network stack, a clean-slate "specialised" stack able to better exploit current hardware architectures and microarchitectures. In the past, I have contributed extensively to the FreeBSD network stack, including leading work to develop scalable multicore support for the TCP stack.
The Capsicum hybrid capability system, which blends capability-system concepts with contemporary UNIX operating-system design. We have upstreamed this work to FreeBSD, which now ships with Capsicum as its native sandboxing model, and Google has developed a Linux adaptation of the model.
Other areas of ongoing interest, and recent projects, include:
System-call interposition concurrency problems: how concurrency can be used to attack interposition-based security wrappers.
The TrustedBSD MAC Framework, a widely deployed OS access-control extensibility framework (now shipped in FreeBSD, Mac OS X, Apple iOS, Junos, and other products).
OpenBSM security-event auditing, the Common Criteria-compliant security logging mechanism shipped in FreeBSD and Mac OS X.
Research interests
I lead a number of research projects spanning the security, computer architecture, and network + operating system research groups at the Computer Laboratory, supported by grants from DARPA, Google, DeepMind, Netapp, Thales E-Security, Arm, and HP Labs. A theme spanning many of my current research areas is the tension between program representation and security, with interests in revising the hardware-software interface, and whole-system implementation of security.
Several of these projects are part of the DARPA-sponsored CTSRD Project in collaboration with Peter G. Neumann at the Computer Science Laboratory at SRI International.
I have additional research interests in the interplay between concurrency and security, operating system access control (especially as relates to software pplication compartmentalisation and capability systems), multi-threaded network stacks, and revisiting a variety of hardware-software interfaces in support of security, networking, and operating system design. Utilising and improving open source platforms for research plays a key role in technology transition for my work.
Capability hardware enhanced RISC instructions (CHERI)
This project is joint between SRI International and the University of Cambridge.
The CHERI architecture provides hardware-assisted in-process sandboxing based on a hybrid capability model. The goal is to support several orders of magnitude greater numbers of sandboxes than current ISAs support -- while still maintaining compatibility with current software designs. CHERI capabilities replace virtual addresses for use in the C language, providing strong integrity protection and provenance validity checking for pointers, bounds checking, and permission protections. We have developed adaptations of the FreeBSD operating system and LLVM compiler suite able to target the architecture. In addition to formal models of the instruction set, we also have a mature pipelined FPGA implementation, and fast Qemu ISA emulation.
Read about CHERI in our Introduction to CHERI or CHERI Instruction-Set Architecture (version 7 technical reports.
We have published work from this project at ISCA 2014, ASPLOS 2015, IEEE S&P 2015, ACM CCS 2015, PLDI 2016, IEEE Micro Magazine 2016, ASPLOS 2017, ICCD 2017, ICCD 2018, POPL 2019, IEEE TC 2019, ASPLOS 2019, IEEE Micro 2019, and IEEE S&P 2020.
Arm has announced Morello, its first experimental CHERI-exdtended processor, System-on-Chip (SoC), and development board. Morello is a 7nm multicore, superscalar processor design that extends the Arm A76 with efficient and scalable capability-based memory protection and software compartmentalization. Morello will ship in late 2021, and be available for academic and industrial research and prototyping.
Bluespec experimental RISC implementation (BERI)
The Bluespec experimental RISC implementation is a new platform for research into the hardware-software interface. Consisting of a 64-bit MIPS ISA FPGA soft core implemented in the Bluespec Hardware Description Language (HDL), a port of the FreeBSD operating system, Clang/LLVM, and a conventional BSD/Apache-licensed software stack, we hope to use BERI to explore a range of new experimental research directions spanning the historically disjoint hardware and software research communities. CHERI is the first search research project. We have had several workshop and conference papers relating to the BERI platform. Brooks Davis (SRI) and I merged BERI support in to FreeBSD in August, 2012, which appeared in FreeBSD 10.0-RELEASE.
Temporally enhanced security logic assertions (TESLA)
Temporally enforced security logic assertions (TESLA) provide compiler-generated run-time instrumentation continuously to continuously validate complex (temporal) security properties, such as check-before-use, eventual audit, and network protocol state machines. We published a paper on TESLA at EuroSys 2014.
Security-oriented analysis of application programs (SOAAP)
The Security-oriented analysis of application programs (SOAAP) provides automated program analysis and transformation technqiues to help software developers deploy application compartmentalisation on sandboxing frameworks such as Capsicum and CHERI. We have had multiple workshop papers on these ideas, including at AHANS 2012 and the Security Protocols Workshop (SPW) 2013, as well as an ACM CCS 2015 paper.
Operating-system network stacks
I have taken a long interest in network-stack structure and performance, including contributing substantially to FreeBSD's multithreaded, multicore network-stack implementation. My past consulting projects in this area include scalable multi-threaded TCP performance and zero-copy support for BPF. My PhD student Ilias Marinos, has been working on network-stack specialisation, the adaptation of network stacks to specific applications and workloads, achieving vastly higher performance than general-purpose stacks. This work has been the subject of papers at HotNets 2013 and SIGCOMM 2014. Bjoern Zeeb, a PhD student jointly supervised by Andrew Moore and myself, is working in network-stack tracing and analysis: what new techniques and tools can we develop to analyse performance and behaviour?
Capsicum: practical capabilities for UNIX

Capsicum: practical capabilities for UNIX: In this work, we developed the notion of a hybrid capability model, blending ideas from research capability system security with commodity UNIX operating systems. Capsicum is intended to support application and library compartmentalisation through extensions to the POSIX API. A key concern in Capsicum is incremental adoption --- we have a long-term vision for capability-oriented security, but wanted to provide a short-term technology adoption path addressing immediate security problems without introducing fundamental incompatibilities (an assumption in prior OS capability systems). This work was first published in USENIX Security 2010, with a version appearing in Communications of the ACM Research Highlights in 2013. We have also published pieces in USENIX's ;login magazine and elsewhere. Capsicum appeared in FreeBSD 9.0, with a more mature implementation and API in FreeBSD 10.0. Google has ported Capsicum to Linux, and continues to support Capsicum development alongside DARPA and the FreeBSD Foundation.
Exploiting concurrency vulnerabilities in system call wrappers
Exploiting concurrency vulnerabilities in system call wrappers: historically, a number of operating system vendors, researchers, and third-party security vendors (such as anti-virus vendors) have relied on system call interposition to augment the OS security model. In this work, I explored inherent concurrency vulnerabilities that exist in the model. We now teach this as an exercise to our Part II security students, who must exploit vulnerabilities in Systrace to deface a web site.
Operating system access control extensibility (MAC Framework)
The TrustedBSD Project: brought features traditionally limited to "trusted" operating systems into open source, including mature security event auditing, extensible kernel access control in support of mandatory access control access control (MAC), and discretionary access control (DAC) extensions such as access control lists (ACLs). These features have been adopted by a number of vendors including the FreeBSD Project, in Apple's Mac OS X and iOS operating systems, Juniper's JunOS, McAfee's Sidewinder firewall, and others. My February 2013 Communications of the ACM retrospective article (and open-access, slightly extended ACM Queue version) cover this evolution in significant detail.
Teaching
I will be on sabbatical for the 2018-2019 academic year, and hence unfortunately not accepting new undergraduate or masters dissertation projects. If you are interested in a 2019-2020 undergraduate or masters project, please contact me by e-mail.
During the 2017-2018 academic year, I taught Part I.B Concurrent and Distributed Systems, and co-taught our masters-level courses in the R209 - Principles and Foundations of Computer Security and R210 - Current Applications and Research in Computer Security. I also taught our masters-level course L41 - Advanced Operating Systems, which teaches advanced topics in operating systems through tracing and performance analysis.
During the 2016-2017 academic year, I taught Part I.B Concurrent and Distributed Systems, and co-taught our masters-level courses in the R209 - Principles and Foundations of Computer Security and R210 - Current Applications and Research in Computer Security. I also taught our masters-level course L41 - Advanced Operating Systems, which teaches advanced topics in operating systems through tracing and performance analysis.
During the 2015-2016 academic year, I taught Part I.B Concurrent and Distributed Systems, and co-teach our masters-level courses in the R209 - Principles and Foundations of Computer Security and R210 - Current Applications and Research in Computer Security. I am also teaching our masters-level course L41 - Advanced Operating Systems, which teaches advanced topics in operating systems through tracing and performance analysis.
During the 2014-2015 academic year, I taught Part I.B Concurrent and Distributed Systems, and co-teach our masters-level courses in the R209 - Principles and Foundations of Computer Security and R210 - Current Applications and Research in Computer Security. I also taught our masters-level course L41 - Advanced Operating Systems, a newly designed course that teaches advanced topics in operating systems through tracing and performance analysis.
During the 2013-2014 academic year, I taught Part I.B Concurrent and Distributed Systems, and co-teach our masters-level courses in the R209 - Computer Security: Principles and Foundations and R210 - Computer Security: Current Applications and Research in Computer Security.
During the 2012-2013 academic year, I taught Part I.B Concurrent and Distributed Systems, and co-taught our expanded masters-level courses R209 - Principles and Foundations of Computer Security and R210 - Current Applications and Research in Computer Security.
During the 2011-2012 academic year, I taught our new masters-level course in R206: Operating and Distributed system Security.
Research student
My current PhD students are Hesham Almatary, Peter Blandford-Baker, Jessica Clarke, Dapeng Gao, Brett Gutstein, Alfredo Mazzinghi, and Domagoj Stolfa.
My past completed PhD students are Lawrence Esswood, Matthew Grosvenor (with Andrew Moore), Ionel Gog (with Ian Lesley), Ilias Marinos, Alex Richardson. I have also played a role in supervising Bjoern Zeeb (with Andrew Moore).
If you are interested in applying to Cambridge for a research-oriented MPhil or PhD in one of my research areas -- including computer security, operating systems, and computer architecture -- please free to get in touch regarding your research topic of interest.
More information on the two programmes, including application requirements and information on initial research proposals, can be found on the MPhil in Advanced Computer Science and PhD in Computer Science pages at the Computer Laboratory. It generally makes sense to get in touch with a potential supervisor before submitting an application, so please do get in touch directly by email (details above).
Postdocs and research assistants
I supervise a team of around a dozen research assistants, research engineers, and post-doctoral researchers. This currently includes Ruslan Bukin, Lawrence Esswood, Edward Napierala, Allison Randal, Alex Richardson, Michael Roe, Andy Turner, and Konrad Witaszczyk.
Programme Committees
I routinely sit on programme committees or external review committees for a number of publication venues in the subfields of security (Oakland / IEEE S&P, USENIX Security, EuroS&P, and ACM CCS) and systems (OSDI, Eurosys, USENIX ATC, and ASPLOS). I have also been a programme-committee member for workshops in the areas of security and systems, including CSET, AHANS, LASER, and others.
Industry and industrial research
Technology transition plays a central role in my research, and I take a particular interest in transition of research through open source systems. I have worked closely with a number of companies, including Apple and Juniper Networks as they have adopted open source systems to both help them engage with the open source community, improved open source software to better meet their needs, and helped them upstream improvements to the open source community. Recent projects have included open source adaptations of Apple's Grand Central Dispatch, collaborative development of the OpenBSM operating system audit framework between Apple and the FreeBSD Project, and work on highly scalable multi-core TCP processing with Juniper. Slightly longer ago, I worked with several companies including Apple and nCircle to help them use and extend the TrustedBSD MAC Framework, a kernel reference monitor now used as the foundation for access control in Mac OS X, iOS, Junos, McAfee's Sidewinder firewall, nCircle's IP360 appliance, and many other products.
Prior to coming to Cambridge, I worked for a series of industrial research labs in the US, including SPARTA ISSO, Trusted Information Systems - Advanced Research and Engineering, and McAfee Research. While there I led a number of network and operating system security research projects for government and industrial sponsors, including DARPA, the US Navy, Apple Computer, and others.
I have received faculty research awards, faculty fellowships, or research and development grants from several companies including Google, Netapp, HP Enterprise / HP Labs, Thales E-Security, and ARM. Industrial partners in DARPA- and EU-funded research projects include SRI International, BAE Systems, and Netapp.
I offer consulting services to companies in the areas of open source integration for products, network stack performance, and operating system audit and access control. A list of past customers and projects is available on request; please contact me directly with any queries.
FreeBSD Project and Foundation
In addition to my academic work, I'm on the board of directors of the FreeBSD Foundation, a US-based non-profit foundation supporting the open source FreeBSD Project. I'm an active contributor to the project, working in the areas of multiprocessor-centric network stacks, operating system security audit, and mandatory access control. I was a member of the FreeBSD Project's elected Core Team for 12 years, and continue to serve as a member of the board of directors of the non-profit FreeBSD Foundation supporting the project. I'm also involved in the project's security officer and release engineering teams.
Publications
Robert N. M. Watson, Jonathan Woodruff, Alexandre Joannou, Simon W. Moore, Peter Sewell, Arm Limited. DSbD CHERI and Morello Capability Essential IP (Version 1), Technical Report UCAM-CL-TR-953, Computer Laboratory, December 2020.
A. Theodore Markettos, John Baldwin, Ruslan Bukin, Peter G. Neumann, Simon W. Moore, and Robert N.M. Watson. Position Paper: Defending Direct Memory Access with CHERI Capabilities. Hardware and Architectural Support for Security and Privacy (HASP) 2020, October 2020.
Robert N. M. Watson, Peter G. Neumann, Jonathan Woodruff, Michael Roe, Hesham Almatary, Jonathan Anderson, John Baldwin, Graeme Barnes, David Chisnall, Jessica Clarke, Brooks Davis, Lee Eisen, Nathaniel Wesley Filardo, Richard Grisenthwaite, Alexandre Joannou, Ben Laurie, A. Theodore Markettos, Simon W. Moore, Steven J. Murdoch, Kyndylan Nienhuis, Robert Norton, Alexander Richardson, Peter Rugg, Peter Sewell, Stacey Son, Hongyan Xia. Capability Hardware Enhanced RISC Instructions: CHERI Instruction-Set Architecture (Version 8), Technical Report UCAM-CL-TR-951, Computer Laboratory, October 2020.
Robert N. M. Watson, Alexander Richardson, Brooks Davis, John Baldwin, David Chisnall, Jessica Clarke, Nathaniel Filardo, Simon W. Moore, Edward Napierala, Peter Sewell, and Peter G. Neumann. CHERI C/C++ Programming Guide, Technical Report UCAM-CL-TR-947, Computer Laboratory, June 2020.
Nathaniel Wesley Filardo, Brett F. Gutstein, Jonathan Woodruff, Sam Ainsworth, Lucian Paul-Trifu, Brooks Davis, Hongyan Xia, Edward Tomasz Napierala, Alexander Richardson, John Baldwin, David Chisnall, Jessica Clarke, Khilan Gudka, Alexandre Joannou, A. Theodore Markettos, Alfredo Mazzinghi, Robert M. Norton, Michael Roe, Peter Sewell, Stacey Son, Timothy M. Jones, Simon W. Moore, Peter G. Neumann, and Robert N. M. Watson. Cornucopia: Temporal Safety for CHERI Heaps. In Proceedings of the 41st IEEE Symposium on Security and Privacy (Oakland 2020). San Jose, CA, USA, May 18-20, 2020.
Kyndylan Nienhuis, Alexandre Joannou, Thomas Bauereiss, Anthony Fox, Michael Roe, Brian Campbell, Matthew Naylor, Robert M. Norton, Simon W. Moore, Peter G. Neumann, Ian Stark, Robert N. M. Watson, and Peter Sewell. Rigorous engineering for hardware security: Formal modelling and proof in the CHERI design and implementation process. In Proceedings of the 41st IEEE Symposium on Security and Privacy (SP), May 2020.
Hongyan Xia, Jonathan Woodruff, Sam Ainsworth, Nathaniel W. Filardo, Michael Roe, Alexander Richardson, Peter Rugg, Peter G. Neumann, Simon W. Moore, Robert N. M. Watson, and Timothy M. Jones. CHERIvoke: Characterising Pointer Revocation using CHERI Capabilities for Temporal Memory Safety. In Proceedings of the 52nd IEEE/ACM International Symposium on Microarchitecture (IEEE MICRO 2019). Columbus, Ohio, USA, October 12-16, 2019.
Robert N. M. Watson, Simon W. Moore, Peter Sewell, and Peter G. Neumann. An Introduction to CHERI, Technical Report UCAM-CL-TR-941, Computer Laboratory, September 2019.
Kyndylan Nienhuis, Alexandre Joannou, Anthony Fox, Michael Roe, Thomas Bauereiss, Brian Campbell, Matthew Naylor, Robert M. Norton, Simon W. Moore, Peter G. Neumann, Ian Stark, Robert N. M. Watson, and Peter Sewell. Rigorous engineering for hardware security: Formal modelling and proof in the CHERI design and implementation process. Technical Report UCAM-CL-TR-940, University of Cambridge, Computer Laboratory, September 2019.
Brooks Davis, Robert N. M. Watson, Alexander Richardson, Peter G. Neumann, Simon W. Moore, John Baldwin, David Chisnall, Jessica Clarke, Nathaniel Wesley Filardo, Khilan Gudka, Alexandre Joannou, Ben Laurie, A. Theodore Markettos, J. Edward Maste, Alfredo Mazzinghi, Edward Tomasz Napierala, Robert M. Norton, Michael Roe, Peter Sewell, Stacey Son, and Jonathan Woodruff. CheriABI: Enforcing valid pointer provenance and minimizing pointer privilege in the POSIX C run-time environment, Technical Report UCAM-CL-TR-932, Computer Laboratory, January 2019.
Robert N. M. Watson, Peter G. Neumann, Jonathan Woodruff, Michael Roe, Hesham Almatary, Jonathan Anderson, John Baldwin, David Chisnall, Brooks Davis, Nathaniel Wesley Filardo, Alexandre Joannou, Ben Laurie, A. Theodore Markettos, Simon W. Moore, Steven J. Murdoch, Kyndylan Nienhuis, Robert Norton, Alex Richardson, Peter Rugg, Peter Sewell, Stacey Son, Hongyan Xia. Capability Hardware Enhanced RISC Instructions: CHERI Instruction-Set Architecture (Version 7), Technical Report UCAM-CL-TR-927, Computer Laboratory, June 2019.
Jonathan Woodruff, Alexandre Joannou, Hongyan Xia, Anthony Fox, Robert Norton, Thomas Bauereiss, David Chisnall, Brooks Davis, Khilan Gudka, Nathaniel W. Filardo, A. Theodore Markettos, Michael Roe, Peter G. Neumann, Robert N. M. Watson, and Simon W. Moore. CHERI Concentrate: Practical Compressed Capabilities. In IEEE Transactions on Computers, 10.1109/TC.2019.2914037, IEEE, 2019.
Brooks Davis, Robert N. M. Watson, Alexander Richardson, Peter G. Neumann, Simon W. Moore, John Baldwin, David Chisnall, Jessica Clarke, Nathaniel Wesley Filardo, Khilan Gudka, Alexandre Joan- nou, Ben Laurie, A. Theodore Markettos, J. Edward Maste, Alfredo Mazzinghi, Edward Tomasz Napierala, Robert M. Norton, Michael Roe, Peter Sewell, Stacey Son, and Jonathan Woodruff. CheriABI: Enforcing Valid Pointer Provenance and Minimizing Pointer Privilege in the POSIX C Run-time Environment. In Proceedings of 2019 Architectural Support for Programming Languages and Operating Systems (ASPLOS’19). Providence, RI, USA, April 13-17, 2019.
A. Theodore Markettos, Colin Rothwell, Brett F. Gutstein, Allison Pearce, Peter G. Neumann, Simon W. Moore, and Robert N. M. Watson. Thunderclap: Exploring Vulnerabilities in Operating System IOMMU Protection via DMA from Untrustworthy Peripherals. In Proceedings of the Network and Distributed Systems Security Symposium (NDSS), 24-27 February 2019, San Diego, USA, 24-27 February 2019.
Kayvan Memarian, Victor B. F. Gomes, Brooks Davis, Stephen Kell, Alexander Richardson, Robert N. M. Watson, and Peter Sewell. Exploring C Semantics and Pointer Provenance. In Proceedings of the 46th ACM SIGPLAN Symposium on Principles of Programming Languages (POPL), Cascais, Portugal, 13-19 January, 2019.
Hongyan Xia, Jonathan Woodruff, Hadrien Barral, Lawrence Esswood, Alexandre Joannou, Robert Kovacsics, David Chisnall, Michael Roe, Brooks Davis, Edward Napierala, John Baldwin, Khilan Gudka, Peter G. Neumann, Alex Richardson, Simon W. Moore, and Robert N. M. Watson. CheriRTOS: A Capability Model for Embedded Devices.. Proceedings of the 2018 IEEE 36th International Conference on Computer Design (ICCD). Orlando, FL, USA, October 7-10, 2018.
Alexandre Joannou, Jonathan Woodruff, Robert Kovacsics, Simon W. Moore, Alex Bradbury, Hongyan Xia, Robert N. M. Watson, David Chisnall, Michael Roe, Brooks Davis, Edward Napierala, John Baldwin, Khilan Gudka, Peter G. Neumann, Alfredo Mazzinghi, Alex Richardson, Stacey Son, and A. Theodore Markettos. Efficient Tagged Memory. Proceedings of the 2017 IEEE 35th International Conference on Computer Design (ICCD). Boston, MA, USA, November 5-8, 2017.
Ilias Marinos, Robert N. M. Watson, Mark Handley, and Randal Ray Stewart. Disk|Crypt|Net: rethinking the stack for high performance video streaming. ACM SIGCOMM 2017 Conference (SIGCOMM'17). Los Angeles, CA, USA, August 21-25, 2017.
Robert N. M. Watson, Peter G. Neumann, Jonathan Woodruff, Michael Roe, Jonathan Anderson, John Baldwin, David Chisnall, Brooks Davis, Alexandre Joannou, Ben Laurie, Simon W. Moore, Steven J. Murdoch, Robert Norton, Stacey Son, Hongyan Xia. Capability Hardware Enhanced RISC Instructions: CHERI Instruction-Set Architecture (Version 6), Technical Report UCAM-CL-TR-907, Computer Laboratory, April 2017.
Robert N. M. Watson, Peter G. Neumann, and Simon W. Moore. Balancing Disruption and Deployability in the CHERI Instruction-Set Architecture (ISA), NEW SOLUTIONS FOR CYBERSECURITY, Shrobe H, Shrier D, Pentland A eds., MIT Press/Connection Science: Cambridge MA. (to appear)
Graeme Jenkinson, Lucian Carata, Thomas Bytheway, Ripduman Sohan, Robert N. M. Watson, Jonathan Anderson, Brian Kidney, Amanda Strnad, Arun Thomas, and George Neville-Neil. Applying Provenance in APT Monitoring and Analysis: Practical Challenges for Scalable, Efficient and Trustworthy Distributed Provenance. Proceedings of the 9th International Workshop on Theory and Practice of Provenance (TAPP'19). Seattle, Washington, June 2017. (to appear)
David Chisnall, Brooks Davis, Khilan Gudka, Alexandre Joannou, Robert N. M. Watson, David Brazdil, Jonathan Woodruff, A. Theodore Markettos, J. Edward Maste, Robert Norton, Stacey Son, Michael Roe, Simon W. Moore, Peter G. Neumann, and Ben Laurie. Sinking the Java security model into the C. Proceedings of the 22nd ACM International Conference on Architectural Support for Programming Languages and Operating Systems (ASPLOS 2017). Xi'an, China, April 8–12, 2017.
Ionel Gog, Malte Schwarzkopf, Adam Gleave, Robert N. M. Watson, and Steven Hand. Firmament: Fast, Centralized Cluster Scheduling at Scale, Proceedings of the 12th USENIX Symposium on Operating Systems Design and Implementation (OSDI 2016), Savannah, GA, USA, November 2016.
Robert N.M. Watson, Robert M. Norton, Jonathan Woodruff, Simon W. Moore, Peter G. Neumann, Jonathan Anderson, David Chisnall, Brooks Davis, Ben Laurie, Michael Roe, Nirav H. Dave, Khilan Gudka, Alexandre Joannou, A. Theodore Markettos, Ed Maste, Steven J. Murdoch, Colin Rothwell, Stacey D. Son, and Munraj Vadera. Fast Protection-Domain Crossing in the CHERI Capability-System Architecture. IEEE Micro vol. 36 no. 5, p. 38-49, Sept.-Oct., 2016
Robert N. M. Watson, Peter G. Neumann, Jonathan Woodruff, Michael Roe, Jonathan Anderson, David Chisnall, Brooks Davis, Alexandre Joannou, Ben Laurie, Simon W. Moore, Steven J. Murdoch, Robert Norton, Stacey Son, Hongyan Xia. Capability Hardware Enhanced RISC Instructions: CHERI Instruction-Set Architecture (Version 5), Technical Report UCAM-CL-TR-891, University of Cambridge, Computer Laboratory, June 2016.
Kayvan Memarian, Justus Matthiesen, James Lingard, Kyndylan Nienhuis, David Chisnall, Robert N. M. Watson, and Peter Sewell. Into the depths of C: elaborating the de facto standards. Proceedings of the 37th ACM SIGPLAN Conference on Programming Language Design and Implementation (PLDI 2016). Santa Barbara, CA, USA, June 2016. PLDI 2016 Distinguished Paper award!
Khilan Gudka, Robert N.M. Watson, Jonathan Anderson, David Chisnall, Brooks Davis, Ben Laurie, Ilias Marinos, Peter G. Neumann, and Alex Richardson. Clean Application Compartmentalization with SOAAP, Proceedings of the 22nd ACM Conference on Computer and Communications Security (CCS 2015), Denver, CO, USA, October 2015.
Robert N. M. Watson, David Chisnall, Brooks Davis, Wojciech Koszek, Simon W. Moore, Steven J. Murdoch, Peter G. Neumann, and Jonathan Woodruff. Capability Hardware Enhanced RISC Instructions: CHERI Programmer’s Guide, Technical Report UCAM-CL-TR-877, University of Cambridge, Computer Laboratory, September 2015.
Robert N. M. Watson, Peter G. Neumann, Jonathan Woodruff, Michael Roe, Jonathan Anderson, David Chisnall, Brooks Davis, Alexandre Joannou, Ben Laurie, Simon W. Moore, Steven J. Murdoch, Robert Norton, and Stacey Son. Capability Hardware Enhanced RISC Instructions: CHERI Instruction-Set Architecture, Technical Report UCAM-CL-TR-876, University of Cambridge, Computer Laboratory, September 2015.
Khilan Gudka, Robert N. M. Watson, Jonathan Anderson, David Chisnall, Brooks Davis, Ben Laurie, Ilias Marinos, Peter G. Neumann, and Alex Richardson. Clean Application Compartmentalization with SOAAP (extended version), Technical Report UCAM-CL-TR-873, University of Cambridge, Computer Laboratory, August 2015.
Matthew P. Grosvenor, Malte Schwarzkopf, Ionel Gog, Robert N.M. Watson, Andrew Moore, Steven Hand, and Jon Crowcroft. Queues don't matter when you can JUMP them!, Proceedings of the 12th USENIX Symposium on Networked Systems Design and Implementation (NSDI), Oakland, California, USA, May 2015. Best paper award!
Robert N. M. Watson, Jonathan Woodruff, Peter G. Neumann, Simon W. Moore, Jonathan Anderson, David Chisnall, Nirav Dave, Brooks Davis, Khilan Gudka, Ben Laurie, Steven J. Murdoch, Robert Norton, Michael Roe, Stacey Son, and Munraj Vadera. CHERI: A Hybrid Capability-System Architecture for Scalable Software Compartmentalization, Proceedings of the 36th IEEE Symposium on Security and Privacy ("Oakland"), San Jose, California, USA, May 2015.
Robert N. M. Watson, David Chisnall, Brooks Davis, Wojciech Koszek, Simon W. Moore, Steven J. Murdoch, Peter G. Neumann, Jonathan Woodruff. Bluespec Extensible RISC Implementation: BERI Software Reference, Technical Report UCAM-CL-TR-869, University of Cambridge, Computer Laboratory, April 2015.
Robert N.M. Watson, Jonathan Woodruff, David Chisnall, Brooks Davis, Wojciech Koszek, A. Theodore Markettos, Simon W. Moore, Steven J. Murdoch, Peter G. Neumann, Robert Norton, and Michael Roe. Bluespec Extensible RISC Implementation: BERI Hardware Reference, Technical Report UCAM-CL-TR-868, University of Cambridge, Computer Laboratory, April 2015.
David Chisnall, Colin Rothwell, Brooks Davis, Robert N.M. Watson, Jonathan Woodruff, Simon W. Moore, Peter G. Neumann and Michael Roe. Beyond the PDP-11: Processor support for a memory-safe C abstract machine, Proceedings of Architectural Support for Programming Languages and Operating Systems (ASPLOS 2015), Istanbul, Turkey, March 2015. Audience pick: best presentation award!
Robert N.M. Watson, Peter G. Neumann, Jonathan Woodruff, Jonathan Anderson, David Chisnall, Brooks Davis, Ben Laurie, Simon W. Moore, Steven J. Murdoch, and Michael Roe. Capability Hardware Enhanced RISC Instructions: CHERI Instruction-Set Architecture, Technical Report UCAM-CL-TR-864, University of Cambridge, Computer Laboratory, December 2014.
Marshall Kirk McKusick, George V. Neville-Neil, and Robert N. M. Watson The Design and Implementation of the FreeBSD Operating System, 2nd Edition, Pearson Education, Boston, MA, USA, September 2014.
Ilias Marinos, Robert N. M. Watson, and Mark Handley, Network Stack Specialization for Performance, Proceedings of ACM SIGCOMM 2014 Conference (SIGCOMM'14), Chicago, IL, USA, August 17–22, 2014.
Jonathan Woodruff, Robert N. M. Watson, David Chisnall, Simon W. Moore, Jonathan Anderson, Brooks Davis, Ben Laurie, Peter G. Neumann, Robert Norton, and Michael Roe. The CHERI capability model: Revisiting RISC in an age of risk, Proceedings of the 41st International Symposium on Computer Architecture (ISCA 2014), Minneapolis, MN, USA, June 14–16, 2014.
Robert N.M. Watson, Peter G. Neumann, Jonathan Woodruff, Jonathan Anderson, David Chisnall, Brooks Davis, Ben Laurie, Simon W. Moore, Steven J. Murdoch, and Michael Roe. Capability Hardware Enhanced RISC Instructions: CHERI Instruction-Set Architecture, Technical Report UCAM-CL-TR-850, University of Cambridge, Computer Laboratory, April 2014.
Robert N.M. Watson, David Chisnall, Brooks Davis, Wojciech Koszek, Simon W. Moore, Steven J. Murdoch, Peter G. Neumann, and Jonathan Woodruff. Capability Hardware Enhanced RISC Instructions: CHERI User’s Guide, Technical Report UCAM-CL-TR-851, University of Cambridge, Computer Laboratory, April 2014.
Robert N.M. Watson, Jonathan Woodruff, David Chisnall, Brooks Davis, Wojciech Koszek, A. Theodore Markettos, Simon W. Moore, Steven J. Murdoch, Peter G. Neumann, Robert Norton, and Michael Roe. Bluespec Extensible RISC Implementation: BERI Hardware Reference, Technical Report UCAM-CL-TR-852, University of Cambridge, Computer Laboratory, April 2014.
Robert N.M. Watson, David Chisnall, Brooks Davis, Wojciech Koszek, Simon W. Moore, Steven J. Murdoch, Peter G. Neumann, and Jonathan Woodruff. Bluespec Extensible RISC Implementation: BERI Software Reference, Technical Report UCAM-CL-TR-853, University of Cambridge, Computer Laboratory, April 2014.
Jonathan Anderson, Robert N. M. Watson, David Chisnall, Khilan Gudka, Brooks Davis, and Ilias Marinos. TESLA: Temporally Enhanced System Logic Assertions, Proceedings of The 2014 European Conference on Computer Systems (EuroSys 2014), Amsterdam, The Netherlands, April 14–16 2014.
Brooks Davis, Robert Norton, Jonathan Woodruff, and Robert N. M. Watson. How FreeBSD Boots: a soft-core MIPS perspective, Proceedings of AsiaBSDCon 2014, 13–16 March, 2014, Tokyo, Japan.
A Theodore Markettos, Jonathan Woodruff, Robert N. M. Watson, Bjoern A. Zeeb, Brooks Davis, Simon W Moore. The BERIpad tablet: open-source construction, CPU, OS and applications, Proceedings of 2013 FPGA Workshop and Design Contest, November 1st–3rd, Southeast University, Nanjing, China.
Ilias Marinos, Robert N. M. Watson, and Mark Handley. Network stack specialisation for performance. Twelfth ACM Workshop on Hot Topics in Networks (HotNets-XII), November, 2013.
William R. Harris, Somesh Jha, Thomas Reps, Jonathan Anderson, and Robert N.M. Watson. Declarative, Temporal, and Practical Programming with Capabilities, IEEE Symposium on Security and Privacy ("Oakland"), May, 2013.
Robert N. M. Watson, Steven J. Murdoch, Khilan Gudka, Jonathan Anderson, Peter G. Neumann, and Ben Laurie. Towards a theory of application compartmentalisation. Security Protocols Workshop, March, 2013.
Robert N. M. Watson. A decade of OS access-control extensibility. Communications of the ACM 56(2), ACM, February 2013.
Robert N. M. Watson. A decade of OS access-control extensibility. ACM Queue 11(1), ACM, January 2013. (Open access, extended version of CACM article.)
Khilan Gudka, Robert N. M. Watson, Steven Hand, Ben Laurie, and Anil Madhavapeddy. Exploring compartmentalisation hypotheses with SOAAP. Proceedings of Adaptive Host and Network Security (AHANS 2012), Lyon, France, September, 2012.
Robert N. M. Watson. New approaches to operating system security extensibility. Technical report UCAM-CL-TR-818, University of Cambridge, Computer Laboratory, April 2012.
Jonathan Anderson and Robert N. M. Watson. Stayin' Alive: Aliveness as an alternative to authentication. In proceedings of the Twentieth International Workshop on Security Protocols (SPW), April 2012.
Robert N. M. Watson, Peter G. Neumann, Jonathan Woodruff, Jonathan Anderson, Ross Anderson, Nirav Dave, Ben Laurie, Simon W. Moore, Steven J. Murdoch, Philip Paeps, Michael Roe, and Hassen Saidi. CHERI: a research platform deconflating hardware virtualization and protection. Runtime Environments, Systems, Layering and Virtualized Environments (RESoLVE 2012), March, 2012.
Steven Smith, Anil Madhavapeddy, Christopher Smowton, Malte Schwarzkopf, Richard Mortier, Robert N.M. Watson, and Steven Hand. The Case for Reconfigurable I/O Channels. Workshop paper, Runtime Environments, Systems, Layering and Virtualized Environments (RESoLVE 2012), March, 2012.
Robert N. M. Watson, Jonathan Anderson, Ben Laurie, and Kris Kennaway. A taste of Capsicum: practical capabilities for UNIX. In Communications of the ACM 55(3), pp. 97-104, March 2012.
Jonathan Anderson, Frank Stajano, and Robert Watson. How to keep bad papers out of conferences (with minimum reviewer effort). Proceedings of the Nineteenth International Workshop on Security Protocols, March 2011
Peter G. Neumann and Robert N. M. Watson. Capabilities Revisited: A Holistic Approach to Bottom-to-Top Assurance of Trustworthy Systems. Proceedings of the Fourth Annual Layered Assurance Workshop, Austin, Texas, December 2010.
Laurel D. Riek and Robert N.M. Watson. The Age of Avatar Realism: When seeing shouldn't be believing. IEEE Robotics and Automation (2010). Vol. 17, Issue 4, pp 37-42.
Robert N. M. Watson, Jonathan Anderson, Ben Laurie, Kris Kennaway. Capsicum: practical capabilities for UNIX. In Proceedings, 19th USENIX Security Symposium 2010, Washington, DC.
Steven J. Murdoch and Robert N. M. Watson. Metrics for security and performance in low-latency anonymity systems. In Proceedings, Privacy Enhancing Technologies Symposium 2008, Leuven, Belgium.
Richard Clayton, Steven J. Murdoch, Robert N. M. Watson. Ignoring the Great Firewall of China. A Journal of Law and Policy for the Information Society, Volume 3, Issue 2, Fall 2007.
Robert N. M. Watson. Exploiting Concurrency Vulnerabilities in System Call Wrappers. In Proceedings, WOOT'07 - First USENIX Workshop on Offensive Technologies, Boston, Massachusetts, USA.
Robert N. M. Watson. How the FreeBSD Project Works. In Proceedings, 2006 EuroBSDCon, Milan, Italy.
Richard Clayton, Steven J. Murdoch, and Robert N. M. Watson. Ignoring the Great Firewall of China. In Proceedings, Privacy Enhancing Technologies Workshop 2006, Cambridge, UK.
Robert N. M. Watson and Wayne Salamon. TrustedBSD OpenBSM: Open Source Security Audit Framework. In Proceedings, 2006 UKUUG Spring Conference, Durham, UK.
Robert N. M. Watson. Introduction to Multithreading and Multiprocessing in the FreeBSD SMPng Network Stack. In Proceedings, 2005 EuroBSDCon, Basel, Switzerland.
Poul-Henning Kamp, Robert N. M. Watson. Building Systems to be Shared, Securely. ACM Queue, July/August 2004.
Robert N. M. Watson, Brian Feldman, Adam Migus, and Chris Vance. The TrustedBSD MAC Framework: Extensible Kernel Access Control for FreeBSD 5.0. In Proceedings, 2003 USENIX Annual Technical Conference, FREENIX Track.
Robert N. M. Watson, Brian Feldman, Adam Migus, and Chris Vance. Design and Implementation of the TrustedBSD MAC Framework. 2003 DARPA Information Security Conference and Exposition (DISCEX III). IEEE.
Sandra L. Murphy, Edward T. Lewis, Robert N. M. Watson. Secure Active Network Prototypes. In Proceedings, 2002 DARPA Active Network Conference and Exposition (DANCE'02). IEEE.
Robert N. M. Watson, TrustedBSD: Adding Trusted Operating System Features to FreeBSD. In Proceedings, 2001 USENIX Annual Technical Conference, FREENIX Track.
Sandra Murphy, Ed Lewis, Ralph Puga, Robert Watson, and Richard Yee. Strong Security for Active Networks. In Proceedings, IEEE OpenArch 2001.
Robert N. M. Watson. Statement for SACMAT 2001 Panel. ACM Workshop on Role Based Access Control. In proceedings of the Sixth ACM Symposium on Access Control Models and Technologies, 2001.
Poul-Henning Kamp and Robert N. M. Watson. Jails: Confining the Omnipotent Root. In Proceedings, SANE 2000 Conference. NLUUG, 2000.
Robert N. M. Watson. Introducing Supporting Infrastructure for Trusted Operating System Support in FreeBSD. In BSDCon 2000 Conference Proceedings. BSDi, 2000.


