Security Group
EMV PIN verification “wedge” vulnerability
Executive summary
The EMV protocol is used worldwide for credit and debit card payments and is commonly known as “Chip and PIN” in the UK. Our analysis of EMV has discovered flaws which allow criminals to use stolen cards without knowing the correct PIN. Where these flaws are exploited – in the “wedge” attack – the receipt and bank records would show that the PIN was correctly verified, so the victim of this fraud may have their request for a refund denied. We have confirmed that this attack works in the UK, including for online transactions (where the terminal contacts the bank for authorization before completing the purchase). It does not apply to UK ATM transactions, which use a different method for PIN verification.
Our academic paper which describes the vulnerabilities in detail, along with ways in which they can be protected against, was circulated privately within the banking industry since early December. The paper will be published at the IEEE Security and Privacy Symposium in May 2010; a working draft is available now.
Background
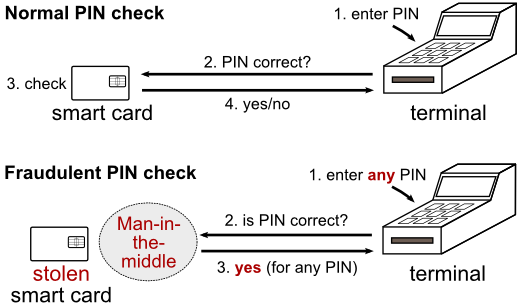
In a normal transaction the customer enters their PIN into the payment terminal, and the terminal sends the PIN to the card to check if it is correct. The card then sends the result to the terminal so that the transaction continues if the PIN was correct (see top part of above figure).
The attack uses an electronic device as a "man-in-the-middle" in order to prevent the PIN verification message from getting to the card, and to always respond that the PIN is correct. Thus, the terminal thinks that the PIN was entered correctly, and the card assumes that a signature was used to authenticate the transaction (see bottom part of above figure).
Questions and answers
Is this the same as the “Yes-card” attack?
Statements from the French banking industry have incorrectly claimed that the attack we have identified is the same as the “Yes-card” attack. Here, a criminal copies a legitimate EMV smart card, but modifies the copy such that it will accept any PIN. The attack we have discovered is different.
The yes-card attack works for transactions for which the point-of-sale terminal does not contact the bank before completing the purchase (an offline transaction). The attack we have discovered works for both online and offline transactions. We have confirmed this by successfully placing an online point-of-sale transaction in the UK, despite entering the wrong PIN.
In this new attack, the criminal must first steal the legitimate card and insert a device, known as a “wedge” between the card and the terminal. It does not involve copying the card.
In what types of transaction does the “wedge” attack work?
We have confirmed this attack to work in online chip-based point of sale transactions, and believe it to work in offline transactions too (although these are rare in the UK). It does not work for ATM transactions, at least in the UK, because a different method of PIN verification is used here. It does not apply to Internet or phone purchases because the PIN is not used to authorize these transactions.
Is this attack too sophisticated for criminals to use?
No, the expertise that is required is not high (undergraduate level electronics) and the equipment can be well hidden without the merchant detecting it. Remember that it only takes a single criminal to design and industrialize the kit required to carry out the attack. Then, other criminals simply buy it online and use it without needing to understand how the attack works
How easy would it be to miniaturize the equipment needed?
For our evaluation of the vulnerability we used cheaply available off-the-self equipment. However, should criminals wish to exploit the vulnerabilities, they would find it easy to create a small and unobtrusive device which would serve the same purpose. We dispute the assertion by the banking industry that criminals are not sophisticated enough, because they have already demonstrated a far higher level of skill than is necessary for this attack in their miniaturized PIN entry device skimmers.
Have you communicated your findings with the banking industry?
Yes, we sent a copy of our findings to various industry representative and regulatory bodies in early December 2009. We have yet to receive any response from the industry, other than through their press releases.
Aren't you helping criminals?
No, security systems improve as vulnerabilities are disclosed to the people that can fix them.
Links
- Newsnight video on YouTube
- New flaws in chip and pin system revealed, Newsnight blog
- Chip and PIN is broken, say researchers, ZDNet UK
- Chip and pin card readers fundamentally flawed, Telegraph
