Security Group
Chip & PIN (EMV) interceptor
Our “Chip & PIN” Point-of-Sale Interceptor has attracted some attention in the German media recently, since TV coverage on ARD TV's Plusminus, by Sabina Wolf, and a corresponding press release from Westdeutscher Rundfunk. This page briefly explains the principle of the interceptor, and what it achieves. Our interceptor is a prototype device which sits between a Point-of-Sale (POS) terminal in a shop and the Chip & PIN card carried by a customer. It listens passively to the electrical signals – “the conversation” – between the chip card and the terminal, and from this can retrieve and store the customer's account number. In the case of the cheaper “Static Data Authentication” (SDA) Chip & PIN cards, which are used by most UK banks, it can also store the customer's entered PIN, when it is sent from the terminal to the card, just after the customer types it in.


Pictures of our prototype interceptor, which can capture account number and PIN from SDA Chip & PIN cards.
Such a device could be miniaturised and concealed as part of one of the roughly 450 000 POS terminals in the UK. It could silently record account details and PINs of all customers using it, unknown to them, and possibly unknown to the shop owner. Such account details and PINs could be used to make counterfeit magnetic stripe cards which could be used in foreign countries which do not have Chip & PIN, or in Chip & PIN countries where the magnetic stripe “fallback” system works side by side with the chip system. In the UK magnetic stripe fallback is possible at some but not all cash machines; also some UK cash machines have not even been upgraded to read chips at all.
Some facts about the interceptor prototype:
- The prototype cost us less than $150 to make (excluding the laptop to read the data out). It could be made much cheaper in quantity. The development time of the prototype was roughly a man-month, from two people with reasonable knowledge of EMV, but no experience programming embedded systems.
- It is made of a small Cypress AN2131QC microcontroller (that is, an embedded computer), a couple of discrete components, and a smartcard monitor board, which simply provides a slot for a smartcard, some wires off the side, and a smartcard shaped probe on the other end.
Some myths about the interceptor:
- It is not a new idea. The risk that a Chip & PIN transaction can be intercepted in this way is well known to the banking industry.
- It does not copy the chip! It only gains enough information from overhearing the conversation to make a magnetic stripe counterfeit.
- It can only overhear the PIN in the case of SDA cards. Dynamic Data Authentication (DDA) cards can accept the PIN in scrambled (encrypted) form, assuming the POS terminal can provide it in this form.
If you would like to learn about the different risks to Point-of-Sale terminals in Chip & PIN, follow the links below, and read on further for more detail…
- You may care to visit homepages of the device creators: Mike Bond, Steven J. Murdoch, where you can find contact details. Also many thanks to Harry Hollis for early help in programming embedded systems.
- The official Chip & PIN website is a starting point to learn about Chip & PIN.
- The authors and Prof. Ross Anderson have created a site describing potential disadvantages of Chip & PIN, titled Chip and SPIN.
- Mike Bond also operates a resource site about Phantom Withdrawals, which contains case studies of customers who have disputed ATM transactions with their banks
Eavesdropping & Relay Attacks
While a smartcard is a very convenient form-factor to carry, it lacks a trusted user interface, unlike for instance a mobile phone. This means the PIN cannot be provided directly to the card, so there is the possibility of eavesdropping en-route. Lack of trusted display means there is no way to confirm who you are doing business with, and what amount is being transacted, so it becomes possible to relay the entire data stream to another location. Let's look at these two well-known drawbacks in more detail.
Eavesdropping POS Terminals
If account and PIN data can be eavesdropped from an EMV transaction at a Point-Of-Sale (POS) terminal, it is easy to make a magnetic stripe card containing that data, for fraudulent use in a foreign country where EMV is not supported. Eavesdropping equipment is already commonplace for unmanned ATMs, usually consisting of a overlay for the card slot and a concealed camera. However there are multiple approaches to eavesdropping POS equipment, each with advantages and drawbacks:
- Camera and Double-swipe
- The most basic approach requires a collusive merchant. The merchant positions a camera with view of the PIN pad, and secretly swipes the card through his own equipment before inserting it into the genuine device.
- Hacked Terminal
- A real POS terminal is opened up and additional circuitry/probes are added to monitor the keypad, and record the data from the smartcard.
- Counterfeit Terminal
- The shell of a genuine POS terminal is used to make a counterfeit, which appears to accept card and PIN, but performs no transaction. Alternatively the counterfeit may pass on the data stream from the smartcard to a hidden genuine terminal, but a physical actuator system to enter the PIN on the real terminal may be required.
- Terminal Skimmer
- A miniaturised interceptor device can be overlayed on top of the smartcard slot on the POS terminal. From this position it can intercept the smartcard stream (capturing account details), and also the PIN. The PIN can be captured here because most European systems are using the cheaper Static Data Authentication EMV cards, which possess no private key, thus the PIN can only be sent in the clear.
The camera and double-swipe approach is definitely workable, but a significant disadvantage is the level of collusion from the merchant required, in order to set up the camera and conceal the second magstripe reader. In addition, a human must go through the video footage study the PINs entered, then correlate with the captured data, which is time consuming and error-prone. Modifying a working terminal requires bypassing of the tamper-resistance, and though this is unlikely to be of a high standard, the attack is still technically very complicated, and requires considerable manual effort for each terminal sabotaged.
The counterfeit terminal approach is appealing, and scales better than a hacked terminal. However the effort required to program a brand-new terminal counterfeit (particularly to drive the receipt printer and LCD display) is substantial. It works well within the business model of giving the customer a free lunch in return for his card and PIN data, but ideally the corrupt merchant would like to mix genuine and counterfeit business over the course of the day. Setting up solenoid actuators so that the PIN can be forwarded is a further complication.
In all, our preferred approach in terms of cost, development time and convenience is to create a skimming device which sits on the smartcard slot, and captures card and PIN data. We created a prototype device using an EZ-USB microcontroller and laptop computer, costing in total comfortably under $150, in development time of approximately one man-month. Our prototype is shown at the top of the page.
It can trivially capture and store account details and PINs for SDA cards in large quantities. Such devices exist for smartcard and POS development, but cost more like $2 500 per device. A finished device could be slotted onto the terminal in seconds, and removed equally quickly should there be a problem. It is thus easier to deploy in environments with only limited collusion from the merchant, and more deniable than installing complex counterfeit terminal equipment or hidden cameras.
Miniaturisation
We have not attempted to miniaturise our prototype as it is only a proof-of-concept, but there is scope to make it considerably smaller. Firstly, the contacts which go between the terminal and card could be hidden in the slot. Secondly, the microcontroller could be hidden somewhere else and short wires used to connect it with the contacts. Finally, the microcontroller board can be shrunk
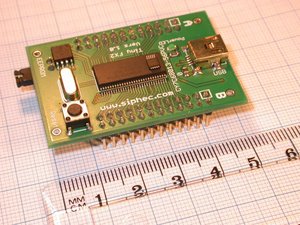
Cypress FX2LP microcontroller, a
smaller, faster variant of the one used in our prototype. The small
chip on top is a Maxim MAX1841
level translator.
The FX2LP microcontroller board above was purchased from Siphec for about $60 and is half the size of our prototype board. This microcontroller runs at double the speed (48 MHz) so eliminates the need for another chip on our prototype. Also, the other large chip, which converts between the 3.3 V used by the microcontroller and 5 V used by smartcards, could be replaced with the MAX1841.
Most of the space in the microcontroller is taken up by the 56 pins on the outside, but we only use 8. A smaller microcontroller, with fewer pins could reduce the size even further.
Smartcard Relay Attacks
Eavesdropping attacks collect account and PIN data for use at a later date, but rely on the magnetic stripe fallback mode of operation, something which might one day be discountinued (though it is unlikely). However if the attackers are well-prepared, they can use the access to the customer's card and PIN in real-time: this is called a relay attack.
For example, as you pay for a meal in a dodgy restaurant using your chip card, the waiter's sabotaged reader could simply forward all the traffic from your card wirelessly to an accomplice at a jewellers on the other side of town. The smartcard data stream would go maybe via GPRS to a PDA in the crooks pocket, then to his fake card, and the captured PIN read out via a headphone in his ear. You think you're paying for lunch, but in fact you're buying the crooks a diamond!
This sort of relay attack is a variation on the counterfeit terminal eavesdropping attack, and we imagine the equipment reqired to deploy it would cost less than $2 000, though substantial development and debugging time would be required. We discuss possible countermeasures to the relay attack problem in a forthcoming paper.
Original text: 7 March 2006