Security Group
Avenues for Attacks
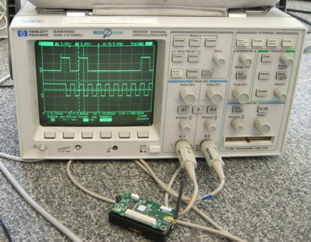
Our goal was to assess practical security of wireless sensor networks on a real, physical system, as opposed to just in theory or through simulations. So we targeted our attacks on the particular platform that our project adopted, namely the MICAz mote from Crossbow, running TinyOS v1.1 and XMesh from MoteWorks 2.0.F, together with the Stargate rev.~1.2 as a gateway.
 A superficial reader might comment that, since we chose the components
and assembled the system ourselves, any security holes we find only
reflect on our own incompetence. On the contrary, the spirit of our
investigation was to imagine that a team of application experts (in
this case civil engineers), assumed to be security-conscious but not
security experts, puts together a system using COTS components,
following the manufacturer's instructions and activating any
recommended security features. We set out to assess the practical
security of the resulting system and to suggest ways of improving it
where appropriate.
A superficial reader might comment that, since we chose the components
and assembled the system ourselves, any security holes we find only
reflect on our own incompetence. On the contrary, the spirit of our
investigation was to imagine that a team of application experts (in
this case civil engineers), assumed to be security-conscious but not
security experts, puts together a system using COTS components,
following the manufacturer's instructions and activating any
recommended security features. We set out to assess the practical
security of the resulting system and to suggest ways of improving it
where appropriate.
Our limited budget and manpower would never have allowed us to carry out a comparative study of all commercially available WSN platforms to determine the most secure one, so that was never a goal. Nonetheless, we believe our results will interesting for users of other platforms too.
 Each of the attacks or exploits described in this section has been
carried out and validated on actual hardware. We report sufficient
details to convince the reader that a vulnerability exists and has
been exploited by us, but stop short of supplying malicious readers
with a cookbook. We also describe how to fix the problem wherever
possible. As a courtesy we supplied a copy of a preliminary version of
this paper to Crossbow in September 2007, to give them a chance to
release security patches based on our advisories.
Each of the attacks or exploits described in this section has been
carried out and validated on actual hardware. We report sufficient
details to convince the reader that a vulnerability exists and has
been exploited by us, but stop short of supplying malicious readers
with a cookbook. We also describe how to fix the problem wherever
possible. As a courtesy we supplied a copy of a preliminary version of
this paper to Crossbow in September 2007, to give them a chance to
release security patches based on our advisories.
 We chose not to concentrate on physical
attacks on the sensors and on the nodes
attached to them, not because we think they are impossible
but because an
attacker with physical access to the sensors could with comparable
effort stage much more destructive attacks on the structure itself,
for example by using explosives. We therefore focus on attacks on the
communication systems, primarily the ad-hoc radio used by the sensor
nodes but also the back-end link from gateway to central server.
We chose not to concentrate on physical
attacks on the sensors and on the nodes
attached to them, not because we think they are impossible
but because an
attacker with physical access to the sensors could with comparable
effort stage much more destructive attacks on the structure itself,
for example by using explosives. We therefore focus on attacks on the
communication systems, primarily the ad-hoc radio used by the sensor
nodes but also the back-end link from gateway to central server.
We studied three broad types of attacks:
- data payload attacks that change the content of data packets;
- network attacks that affect the functionality of the network, for example by preventing communication, taking down specific links, modifying the routing topology or rewriting the firmware of a node; and
- system attacks, potentially the most damaging, in which the attacker exploits a vulnerability in one part of the system architecture (e.g. the wireless network) to gain control of other parts (e.g. the gateway or the central computer).
Attack mechanisms we employed included jamming (at various degrees of selectivity and at different layers in the stack), replay attacks, packet injection or corruption (where the injected or malformed packets were specifically crafted to probe for vulnerabilities or to trigger known vulnerabilities) and ACK spoofing.
Basic description of the attacks and our implementations of the attacks is in our paper Steel, Cast Iron and Concrete: Security Engineering for Real World Wireless Sensor Networks, published at Applied Cryptography and Network Security 2008 conference.
