Course material 2010–11
Security I
Lecturer: Dr M.G. Kuhn
No. of lectures: 12
Prerequisite courses: Discrete Mathematics II, Operating Systems
This course is a prerequisite for Security II.
Aims
This course covers essential concepts of computer security and cryptography.
Lectures
- Cryptography. Introduction, terminology, finite rings and
fields, modular arithmetic, GF(
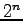 ), pseudo-random functions and
permutations.
), pseudo-random functions and
permutations.
- Classic ciphers. Vigenére, perfect secrecy, Vernam,
computational security, Kerckhoffs’ principle, random bit sources.
- Stream ciphers. Attacking linear-congruential RNGs and
LFSRs, Trivium, RC4.
- Block ciphers. SP networks, Feistel/Luby-Rackoff structure,
DES, AES, modes of operation, message authentication codes.
- Secure hash functions. One-way functions, collision
resistance, Merkle-Damgård construction, padding, birthday
problem, MD5, SHA, HMAC, stream authentication, Merkle tree,
Lamport one-time signatures.
- Asymmetric cryptography. Key-management problem,
signatures, certificates, PKI, discrete-logarithm problem,
Diffie-Hellman key exchange, ElGamal encryption and signature,
hybrid cryptography.
- Entity authentication. Passwords, trusted path, phishing,
CAPTCHA. Authentication protocols: one-way and challenge-response
protocols, Needham-Schroeder, protocol failure examples, hardware
tokens.
- Access control. Discretionary access control matrix, DAC in
POSIX and Windows, elevated rights and setuid bits, capabilities,
mandatory access control, covert channels, Clark-Wilson integrity.
- Operating system security. Trusted computing base, domain
separation, reference mediation, residual information protection.
- Software security. Malicious software, viruses. Common
implementation vulnerabilities: buffer overflows, integer overflows,
meta characters, syntax incompatibilities, race conditions,
unchecked values, side channels.
- Network security. Vulnerabilities of TCP/IP, DNS.
HTTP authentication, cookies, cross-site scripting, browser
sandboxes. Firewalls, VPNs.
- Security policies and management. Application-specific
security requirements, targets and policies, security management,
BS 7799.
Objectives
By the end of the course students should
- be familiar with core security terms and concepts;
- have a basic understanding of some commonly used attack
techniques and protection mechanisms;
- have gained basic insight into aspects of modern cryptography
and its applications;
- appreciate the range of meanings that “security” has across
different applications.
Recommended reading
* Paar, Ch. & Pelzl, J. (2010). Understanding cryptography. Springer.
Gollmann, D. (2006). Computer security. Wiley (2nd ed.).
Further reading:
Anderson, R. (2008). Security engineering. Wiley (2nd ed.).
Stinson, D. (2005). Cryptography: theory and practice. Chapman & Hall/CRC (3rd ed.).
Cheswick, W.R., Bellovin, S.M. & Rubin, A.D. (2003). Firewalls and Internet security: repelling the wily hacker. Addison-Wesley (2nd ed.).
Garfinkel, S., Spafford, G. & Schwartz, A. (2003). Practical Unix and Internet security. O’Reilly (3nd ed.).
