SECURE
Overview
SECURE is an IST Global Computing project to create security mechanisms for the Internet, based on explicit models of trust and risk. SECURE itself is an acronym which stands for Secure Environments for Collaboration among Ubiquitous Roaming Entities (and is in no way contrived...)
The project is a distributed, collaborative one and includes a number of researchers from the Cambridge University Computer Lab. To the right you can see several members of the SECURE team captured in their natural habitat, sightseeing around Europe.
Project Background
On the Internet we encounter huge numbers of unknown entities whom it would be beneficial to interact with. These are new peer to peer interactions, not the normal kind between clients and trusted servers. The problem is that many of these possible transactions involve risks of some sort. We clearly can't assume that everyone is trustworthy, but traditional security policies (trust nobody until they have been authenticated) are just too inconvenient for users to bother with.
Applications
Here are some of the relevant application areas:
- Micropayments for web services (maps, photos, addresses, weather, etc.);
- Electronic cash, vending machines, tollbooths, mobile phones;
- Shared city guides;
- Collaborative gaming;
- Ad-hoc wireless routing;
- Spam filtering, call handling;
- Distributed backup/file systems.
The SECURE Framework
The SECURE Framework In SECURE, we assume that principals can be identified in some way (e.g. by a public key), even though we have no idea whom they are in real life. We then monitor the outcome of interactions with them, and derive a trust value based on their observed behaviour. Our trust in each principal is used to predict the likelihood that they will behave well in future.
When the user wishes to perform a transaction with another principal, the system runs a risk analysis based on the cost or benefit of the possible outcomes and on that principal's trust value. It then decides whether it is advisable to permit the action or not. All of this is automated of course, so the user can simply click on a link without worrying about the potential risks involved.
In many cases one may come across complete strangers, for whom you have no observations or trust value as yet. A key part of the system is the ability to request recommendations from others. This allows the formation of a trust value based on other principals' experience. Recommendations are interpreted in the light of our meta-trust in the recommender, which measures their reliability and truthfulness.
Specialist research areas
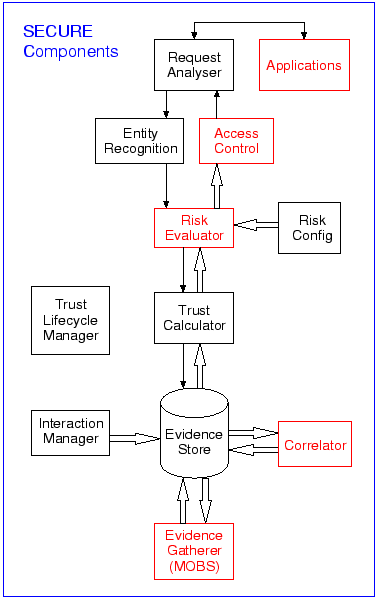
The Cambridge group has a strong background in event architectures (CEA) and access control (OASIS). Our research within this project focuses on risk modelling, security policy, access control and distributed evidence stores. The components we are working on are highlighted in red in the diagram to the right.
Additionally, Brian is researching automatic computerized contracts for negotiating and controlling resource usage in distributed systems. A trust model is used to enforce these promises, and also allows trust delegation through cryptographic certificates. See this paper for details (citation).
Partners
David and Liz on a swingboat. Five different Universities are involved with the SECURE project, and there is a close collaboration between them:
- Opera Group, University of Cambridge, England
- Distributed Systems Group, Trinity College Dublin, Ireland
- SmartLab, University of Strathclyde, Glasgow, Scotland
- BRICS, University of Aarhus, Denmark
- Object Systems Group, University of Geneva
The image to the right shows our intrepid SECURE researchers taking time out to stress test an antique children's swingboat ride. We were pretty surprised the attendant let us have a go. The girl in blue is about fourteen years old and looks concerned because David and Liz are leveraging both their superior gravity and childishness to go a lot higher than her.
Links
For more information about the project, please visit the central SECURE web page.
