Next: What is the IMG
Up: Other Credibility Problems
Previous: Reasons for algorithm choice
In addition to its lack of awareness of the cryptographic algorithms available
in the open literature, the IMG strategy contains what we believe are further
errors, of which the more obvious include the following.
- The claim that digital signatures can only be generated using asymmetric
techniques (p 55 and p 61) is false. Lamport invented signatures based on hash
functions before any public key algorithms were published [30, 50],
and the military used authenticators based on concatenated encryption by the
1970's [78]. The first of these references is cited in a book written
by the IMG's senior adviser ([18] p 393). In recent years, there have
been many research results on this topic (see, e.g., [19]).
- Another claim that by the strategy document that is not supported by
recent research is the assertion on p 57 that by `reason of very large
scale, it will be essential for the NHS to have a Key Management infrastructure
that includes the use of asymmetric key management methods'. This is a non
sequitur. The scalability of trust structures and mechanisms has recently been
widely discussed at research conferences, and it is now well understood that
both symmetric and asymmetric key management scale in about the same way.
Asymmetric systems may appear at first sight to be cheaper but this is only the
case so long as the work undertaken by users and the cost of a certificate
revocation service are excluded from the calculation. Once they are included,
both approaches cost each of n principals about
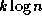 effort; no
convincing evidence has been adduced to show that the value of the constant k
differs significantly from one technology to the other.
effort; no
convincing evidence has been adduced to show that the value of the constant k
differs significantly from one technology to the other. - The claim that there are only two options for key management, namely RSA
and Diffie Hellman (p 21) is wrong. Even without reference to recent research,
there is an established product called Kerberos that would be a much cheaper
option in the event that the IMG persists in its wish to centralise key
management in a small number of online servers. In fact, the security
architecture proposed by GCHQ, and which IMG appears to be trying to adopt or
adapt, gives no more functionality than Kerberos, but at much greater cost.
- The claim that TTPs will `add only a negligible amount of additional
network traffic' is unconvincing. If, for example, the GCHQ protocol were
used, then the quantity of extra network traffic could be considerable:
whenever two principals in different domains communicate, a reference must be
made to both of their TTPs to get a key of the day. IMG may have intended that
the whole of the NHS would be in a small number of security domains; they have
claimed that professional bodies such as the GMC and the UKCC would be the TTPs
[86]. In that case, the use of the GCHQ protocol could mean that a
doctor who exchanged messages regularly with a nurse (perhaps in his own
practice) would have to send messages to both the GMC and the UKCC to obtain
fresh key material at the start of each day.
- Various safety aspects are neglected. For example, the use of digital
signatures to protect the integrity of clinical data will be best supported by
integration with clinical EDIFACT messages rather than by enclosing these in an
envelope. In the latter case, the signature may be discarded before the message
reaches the destination clinical system, and various interactions with X.400
might also have to be considered. Both safety and medico-legal considerations
suggest that the digital signature facilities be well integrated with clinical
applications rather than hidden invisibly behind an application programming
interface, as suggested by the IMG on p 16 and at the June meeting.
- The interaction with access control will probably require that both
encryption and key management are also integrated with EDIFACT messages for
similar reasons.
- The claim by the IMG at the July meeting that messages should be first
encrypted and then signed is mistaken, as with many systems the signed
ciphertext can be decrypted to a different plaintext using a different key
[5]. Messages should first be signed and then encrypted, just as
letters are first signed and then sealed in an envelope. Quite apart from the
technical security reasons for this, signatures in healthcare often have to be
verified by third parties, who will not normally have access to the decryption
keys of the original recipient.
- The strategy document makes a number of claims about PGP on p 56 which
are incorrect, such as that it does not integrate well with standard email
packages. In fact, it is integrated with far more mail systems than any other
encryption program. It is also claimed to be unsuitable for a large
organisation; yet the UK academic network, UKERNA, aims to use it for its
security infrastructure. The claim that PGP would need modification by
suppliers to support TTPs is also untrue [67].
- The NHS strategy claims security advantages for unpublished algorithms,
but then suggests an algorithm that will be made available in software. As
shown by RC2 and RC4, it is only a matter of time before such algorithms are
reverse engineered and published. If IMG believes in the alleged advantages of
unpublished algorithms, then logically their strategy should have recommended
an algorithm available only in tamper resistant hardware such as Skipjack.
- On p 23, the IMG strategy mentions that independent advice should be
taken on the strength of Red Pike. Yet on p 26 it states that the people who
evaluate the algorithm have to be acceptable to its owners. Independence can be
hard to achieve under these circumstances.
- The strategy's overall view that security is largely a matter of
algorithm choice is mistaken. The engineering aspects are far more important
[3] and these are largely neglected in the strategy.
- The claim on p 50 that cryptography must be done at either the link or
the application layer is wrong; session level encryption is common, and network
layer encryption is about to be introduced to the Internet through IPSEC. In
addition, the claim on p 51 that end-to-end security services can be located
between the link and network layer is incorrect. There is further lack of
clarity over the layer at which encryption will take place, and compatibility
between services at different layers, in the following few pages and between
there and p 53.
- the claim on p 28 that `increasingly NHS users will be using smart cards
for system access' is a surprise, given the IMG decision to endorse
non-smartcard authentication devices from SecurID and Digital Pathways for
remote login, and pilots of medical records using optical rather than smart
cards.
- The implication that there will be a National Public Key Infrastructure
that will manage all cryptographic keys in Britain may reflect the desires of
GCHQ but is impractical [12].
- Further unsupported minor assumptions in the strategy include:
- that health care managers, rather than clinical professionals, are
responsible for the security of personal health information (p 41);
- that contracting data is not identifiable (p 43);
- that only two principals will ever be party to a secure session (p 57),
which would exclude secure electronic case conferences.


Next: What is the IMG
Up: Other Credibility Problems
Previous: Reasons for algorithm choice
Ross Anderson
Mon Oct 6 12:47:34 BST 1997